With the rapid increase in the popularity of the Internet, it was only a matter of time before services began becoming the target of cyber criminals. Extortion under the threat of DDoS is on the rise with teenagers able to launch 300+Gbps attacks from a home machine and a few £10 VPS’s.
Outfits such as DD4BC (DDoS 4 Bitcoin) & Armada Collective have managed to rake in significant sums of money without actually carrying out any substantial DDoS’s. So why were they successful? Well in part because services on the Internet are extremely exposed and vulnerable; It’s easiest to describe them as a person in a high-vis jacket stood in the middle of a battlefield, sooner or later that person’s going to get shot, and that ever-looming threat has some service providers woeful of rocking the boat.
How we deal with DDoS’s
As the Technical Director for Call27, it’s my job to help pro-actively identify potential weak points across our network and co-ordinate strategies to help keep our services online no matter what. The Internet is a place that was built on a foundation of trust and is now retrospectively being patched to try and close these loopholes, but it’s a slow process.
In early 2016 a customer of ours approached us having received a DDoS threat from the Armada Collective. At the time their datacenter presence was isolated to Manchester. They enquired with a few DDoS mitigation services, but many were only able to deliver the service in London.
We stepped up to the challenge and were able to orchestrate a mitigation service for them with only a few days notice, provided over our existing 10Gbps link from London (Harbour Exchange 6/7) to Manchester (Equinix Williams).
Today we are the target of DDoS’s at an increasing frequency and our upstream supplier NTT can mop up the largest for us with ease ensuring our services stay online no matter what. However enabling NTT scrubbing is a process requiring manual intervention.
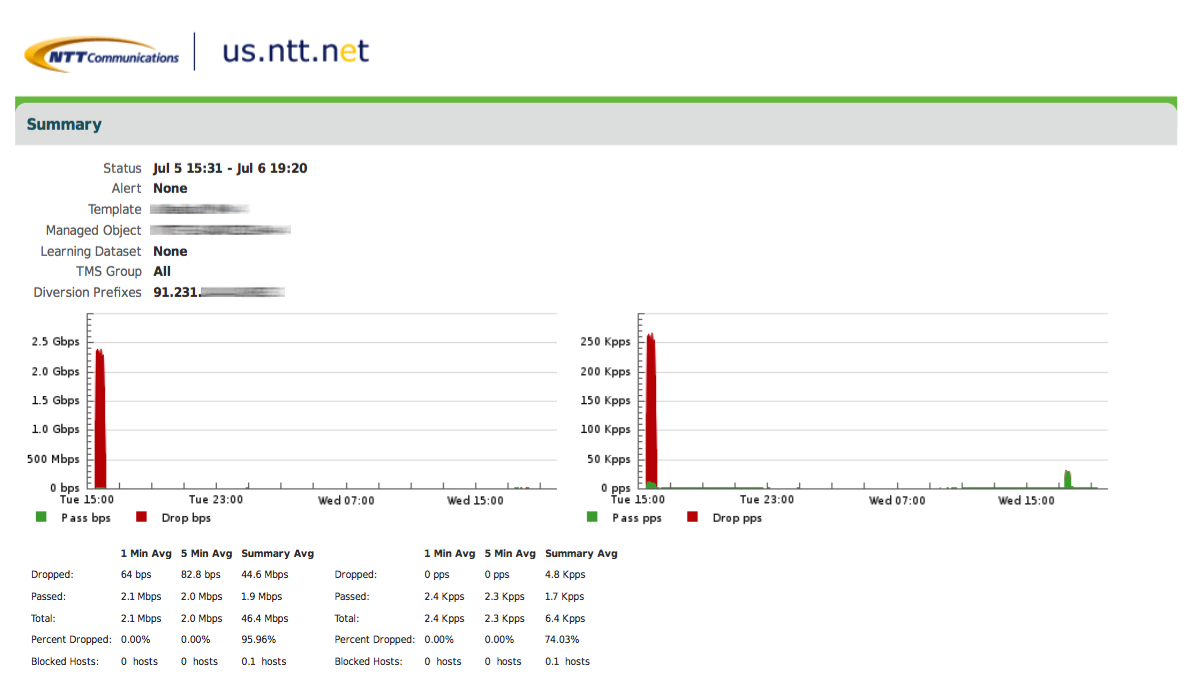
An example DDoS directed at one of our customers servers, handled by NTT. Peak at around 2.4Gbps.
Plans for the short-term future
This manually reactive process puts a dependent resource on a Technician to intervene. Moving forward our short-term goal is to automate the detection method and scrub some of the smaller DDoS’s (<10Gbps) at our edge. Inbound traffic to our edge will be cloned to a DDoS detection unit. This brings detection down to seconds and rules can then trigger filtering for the targetted IP or trigger a request to NTT to intervene if the attack is too large. This new system will see the whole process shortened significantly.
We look forward to publishing part 2 of this blog entry once we’ve gone through an extensive testing process of the new system.
